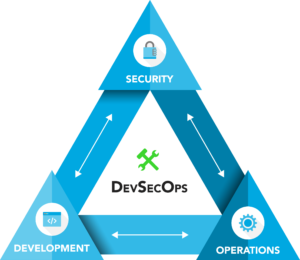
Focal Point helps companies secure their application lifecycle by applying comprehensive security measures at every step – from initial planning to deployment. Whether you need help evaluating, testing, or building a deployment pipeline, or an assessment of your overall DevSecOps strategy, our team has the knowledge and proven experience to support your organization without compromising on quality or speed of delivery.